Securing Legacy Systems - JHUISI
Overview
This exercise demonstrates how Snort and similar inline intrusion detection / prevention systems can be used to help secure legacy software by walking them through an environment that includes an extremely insecure application.
Depending on their skill level students will be asked to analyze network the network traffic produced by this program, to write Snort rules to protect against known attacks against this program and to create a sample attack against this program which they will be asked to guard against.
Recommended Reading
The following information may be useful in completing this exercise.
- Short summary of Snort on Wikipedia
- SYN flood attacks in the The Snort Manual
- A guide to creating Snort Preprocessors
Introduction
When working in the field of network security it is not always possible to ensure the security of legacy applications. Many businesses and organizations use systems that are known to be highly insecure and will continue to do so for the foreseeable future as it would not be cost effective to replace or modify these programs. As such the best we can do to improve the security of these systems is to place them behind filters that can be controlled.
In this exercise you will be using Snort to help secure a highly insecure application without modifying the application itself. This application functions as a simple password protected file server for plain text documents, and it is up to you to use Snort to help protect this information.
This network is broken into three chunks. The first chunk contains the work environment which houses the legacy server along with a single client machine. This network is protected by the Snort router, which is set not to permit any traffic through at at the start of this exercise. The second network contains a single outsider machine. Finally, the third contains two client computers. All of these networks are connected to each other using a single router.
Assignment Instructions
Setup
- If you don't have an account, follow the instructions in the introduction to DeterLab document.
- Log into DeterLab
- Create an instance of this exercise by following the instructions here, using snort as Lab name. Your topology will look like below:
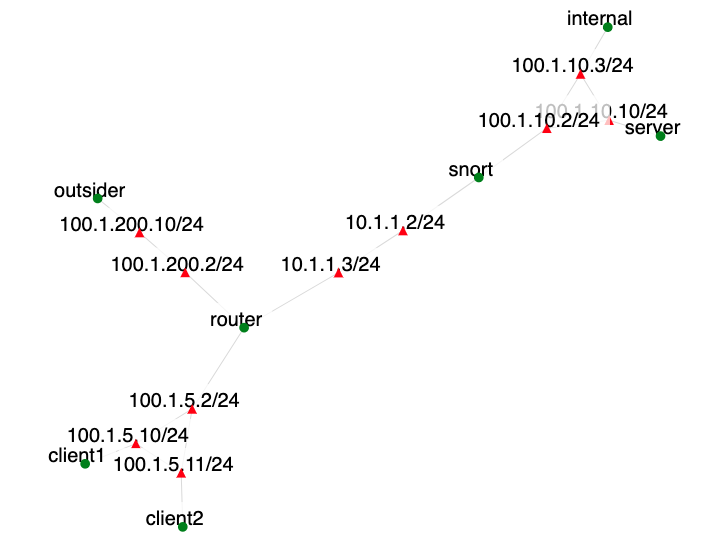 .
.
- After setting up the lab, access your nodes.
Basic Tasks
Start Snort Without Rules
- Connect to the snort node and modify /etc/snort/snort.debian.conf to set the DEBIAN_SNORT_HOME_NET to 100.1.10.0/24. Then type:
sudo snort --daq nfq -Q -v - On client1 node type:
ftp bob ...enter "anonymous" as username ...enter any string as password get ducky.xmlYou should see a large number of packets being reported by Snort. On router node run:tcpdump -i ethX -nn -s 0 -X
replacing ethX with the interface with the IP address 10.1.1.3.Questions:
- What happens to the traffic to client1 when Snort is not running?
- Is this a good thing?
- Can you reconstruct contents of ducky.xml on router node?
- Based on Snort's output what can you say about the application? What port does it connect to?
- What does the "-Q" option do in Snort? Use man page to find out.
- What does the "--daq nfq" option do in Snort? Use man page to find out.
Write Rules to Guard Against Simple Requests
- In that terminal where snort is running stop it by using ctrl + c.
- Use any text editor to edit /etc/snort/rules/local.rules.
Add the following snort rule that prevents .xml files from being sent out,
reject tcp 100.1.0.0/16 ANY -> 100.1.10.10 [Port from Question 3] (msg: "XML Read Attempt Detected"; sid:1; content:".xml";)
- Using this rule as an example write a rule that prevents classified data from being sent to the outsider computer, but does not prevent it from being sent to any other computers. Classified data is stored in files with names that share a prefix "classified".
- Start snort using your new rule with the command:
sudo snort --daq nfq -Q -c /etc/snort/snort.conf -A console - Log onto client1, client2 and outsider to see if these rules worked. Try using ftp on these nodes to read classified files.
Questions:
- What happens to FTP traffic from client1 when you run snort? Show the FTP output as client1 tries to exfiltrate "classified.txt" file.
- What rule did you use to secure the "classified" files?
- Capture and compare the network traffic for the serverwhen filtering these results using your configuration file and when no file is used. Can you recover the contents of classified files?
- Can you think of any others files or extensions that should be filtered against? You can see what files server node has in its /srv/ftp folder.
Attack Defense
- Make sure you have your filtering rule engaged on Snort
- On outsider node install nmap:
apt update -y apt install nmap -y - Run:
nmap 100.1.10.0/24to scan the server network, and check your Snort output. - On outsider node run:
ping -f serverto generate a flood of ICMP traffic to server node. Create a new Snnort rule that detects any ICMP packets sent from the outside into the network.
Questions:
- Show Snort alerts for NMAP.
- Show your new rule to detect ICMP traffic.
- Show Snort alerts for ICMP flood (a few alerts are enough).
- Try changing the action in the new rule to "reject" instead of "drop". What does this do to the traffic and why do you think this is? Is this a good or a bad thing?
What can go wrong
- Nodes Cannot Communicate with Server If the server or route cannot communicate with each other when Snort running, make sure that the routing table is correct. You can check the routing table with the command "route" on both of the computers.
Submission Instructions
You should submit a document with the following items (label each section):- An explanation of how Snort can be used to protect legacy systems
- Answers to all the questions in this file